A company is deploying a DIP solution and scanning workstations and network drives for documents that contain potential Pll and payment card data. The results of the first scan are as follows:
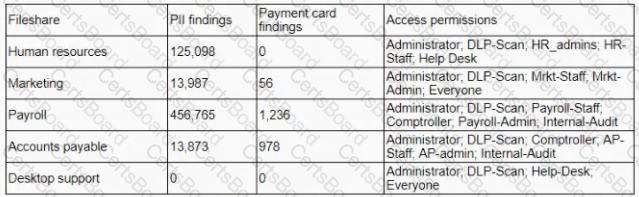
The security learn is unable to identify the data owners for the specific files in a timely manner and does not suspect malicious activity with any of the detected files. Which of the following would address the inherent risk until the data owners can be formally identified?
A system administrator recently conducted a vulnerability scan of the internet. Subsequently, the organization was successfully attacked by an adversary. Which of the following in the MOST likely explanation for why the organization network was compromised?
A network service on a production system keeps crashing at random times. The systems administrator suspects a bug in the listener is causing the service to crash, resuming in the a DoS. Which the service crashes, a core dump is left in the /tmp directory. Which of the following tools can the systems administrator use to reproduction these symptoms?
A developer has executed code for a website that allows users to search for employees’ phone numbers by last
name. The query string sent by the browser is as follows:
http://www.companywebsi te.com/search.php?q=SMITH
The developer has implemented a well-known JavaScript sanitization library and stored procedures, but a
penetration test shows the website is vulnerable to XSS. Which of the following should the developer implement
NEXT to prevent XSS? (Choose two.)


