During a routine security audit, an organization's security team detects an unusual spike in network traffic originating from one of their internal servers. Upon further investigation, the team discovered that the server was communicating with an external IP address known for hosting malicious content. The security team suspects that the server may have been compromised. As the incident response process begins, which two actions should be taken during the initial assessment phase of this incident? (Choose two.)
Which two tools conduct network traffic analysis in the absence of a graphical user interface? (Choose two.)
A threat actor has successfully attacked an organization and gained access to confidential files on a laptop. What plan should the organization initiate to contain the attack and prevent it from spreading to other network devices?
Refer to the exhibit.
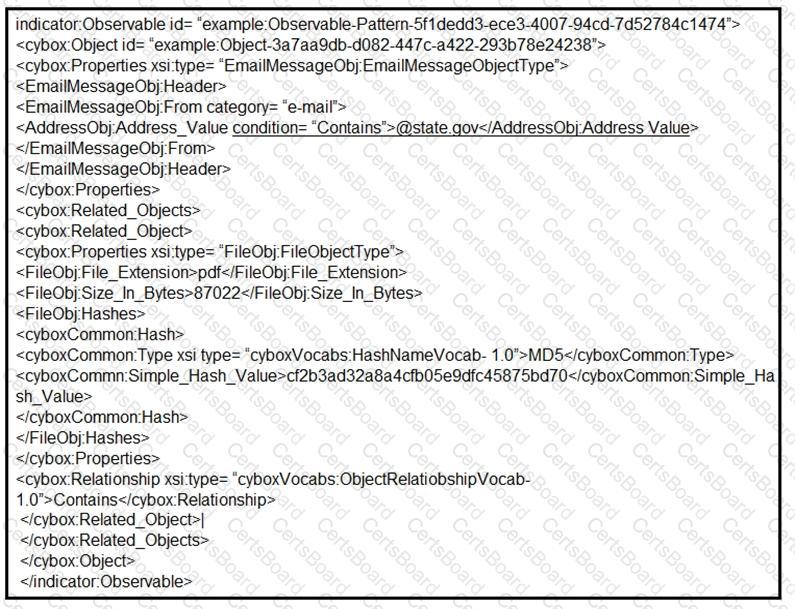
Which two actions should be taken as a result of this information? (Choose two.)
What is an issue with digital forensics in cloud environments, from a security point of view?
Refer to the exhibit.
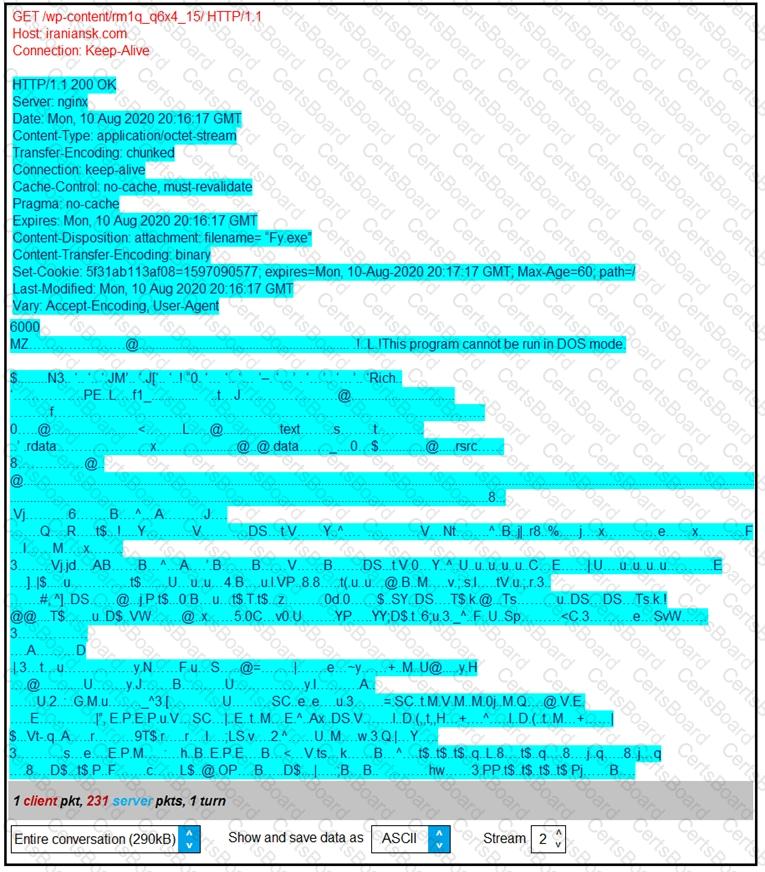
According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)


