During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
Which two advantages does FortiSASE bring to businesses with multiple branch offices? (Choose two.)
Which FortiSASE feature ensures least-privileged user access to all applications?
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which three setups will achieve the above requirements? (Choose three.)
A customer wants to upgrade their legacy on-premises proxy to a could-based proxy for a hybrid network. Which FortiSASE features would help the customer to achieve this outcome?
Refer to the exhibit.
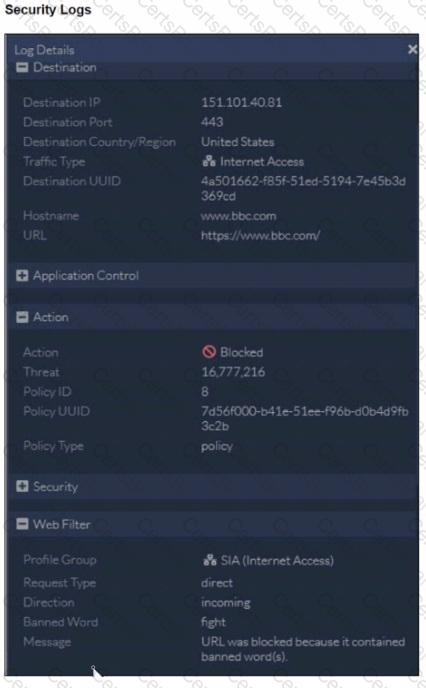
To allow access, which web tiller configuration must you change on FortiSASE?
Which two deployment methods are used to connect a FortiExtender as a FortiSASE LAN extension? (Choose two.)
An organization must block user attempts to log in to non-company resources while using Microsoft Office 365 to prevent users from accessing unapproved cloud resources.
Which FortiSASE feature can you implement to achieve this requirement?
Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)


