Cellebrite’s Physical Analyzer will conduct a Quick Scan for images, which goes through and carves files that may have been deleted from the device. When carving for image files, which of the following methods is most effectively used to recover data?
An Android device user is known to use Facebook to communicate with other parties under examination.
There is no evidence of the Facebook application on the phone. If there was Facebook usage where would an examiner expect to find these artifacts?
Which artifact must be carved out manually when examining a file system acquisition of an Android device?
Exhibit:
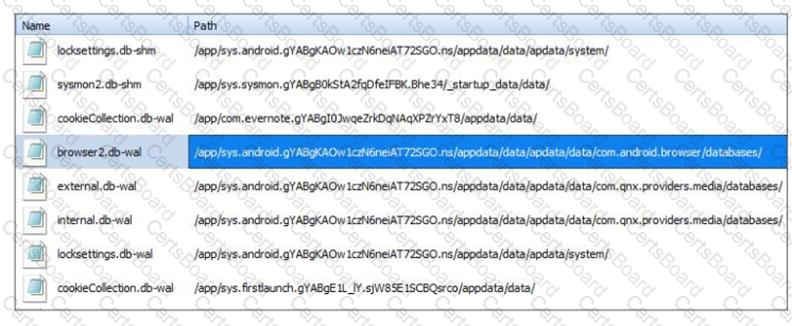
Where can an analyst find data to provide additional artifacts to support the evidence in the highlighted file?
When conducting forensic analysis of an associated media card, one would most often expect to find this
particular file system format?
Using an emulator and running an application through a series of processes to figure out how it would behave on an actual device is called:
Cellebrite Physical Analyzer uses Bit Defender to scan for malware by flagging files who have known bad hash values. This is an example of which type of mobile malware detection?


