A company estimates a loss of $2,374 per hour in sales if their website goes down. Their webserver hosting site’s documented downtime was 7 hours each quarter over the last two years. Using the information, what can the analyst determine?
When attempting to collect data from a suspected system compromise, which of the following should generally be collected first?
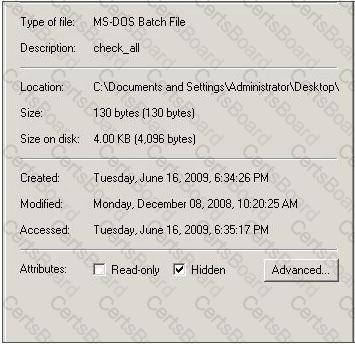
Which command tool can be used to change the read-only or hidden setting of the file in the screenshot?
Monitoring the transmission of data across the network using a man-in-the-middle attack presents a threat against which type of data?
A security device processes the first packet from 10.62.34.12 destined to 10.23.10.7 and recognizes a malicious anomaly. The first packet makes it to 10.23.10.7 before the security devices sends a TCP RST to 10.62.34.12. What type of security device is this?
You have been tasked with searching for Alternate Data Streams on the following collection of Windows partitions; 2GB FAT16, 6GB FAT32, and 4GB NTFS. How many total Gigabytes and partitions will you need to search?
An outside vulnerability assessment reveals that users have been routinely accessing Gmail from work for over a year, a clear violation of this organization’s security policy. The users report “it just started working one day”. Later, a network administrator admits he meant to unblock Gmail for just his own IP address, but he made a mistake in the firewall rule.
Which security control failed?
To detect worms and viruses buried deep within a network packet payload, Gigabytes worth of traffic content entering and exiting a network must be checked with which of the following technologies?
Following a Digital Forensics investigation, which of the following should be included in the final forensics report?


