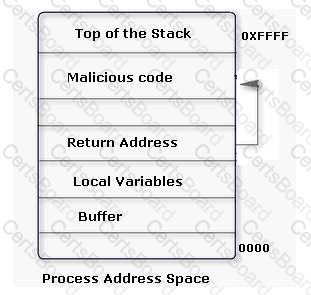
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
Which of the following tools can be used as a countermeasure to such an attack?
Which of the following firewalls filters the traffic based on the header of the datagram?
Which of the following techniques allows probing firewall rule-sets and finding entry points into the targeted system or network?
Which of the following is a maintenance protocol that permits routers and host computers to swap basic control information when data is sent from one computer to another?
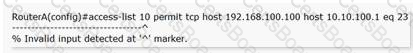
Choose the best explanation for the resulting error when entering the command below.
Mark works as a Network Security Administrator for BlueWells Inc. The company has a Windowsbased network. Mark is giving a presentation on Network security threats to the newly recruited employees of the company. His presentation is about the External threats that the company recently faced in the past. Which of the following statements are true about external threats?
Each correct answer represents a complete solution. Choose three.
John works as the Security Manager in PassGuide Inc. He wants to protect his network from a variant of the Denial-of-Service (DoS) attack. When the rulebase is enabled for protection, the IDP engine checks the traffic that exceeds the traffic thresholds. Which of the following rulebases is used for this purpose?
An organization has more than a couple of external business, and exchanges dynamic routing information with the external business partners. The organization wants to terminate all routing from a partner at an edge router, preferably receiving only summary routes from the partner. Which of the following will be used to change all partner addresses on traffic into a range of locally assigned addresses?
Adam works as a professional Computer Hacking Forensic Investigator. He works with the local police.
A project has been assigned to him to investigate an iPod, which was seized from a student of the high school. It is suspected that the explicit child pornography contents are stored in the iPod. Adam wants to investigate the iPod extensively. Which of the following operating systems will Adam use to carry out his investigations in more extensive and elaborate manner?