Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
Nathan works as a professional Ethical Hacker. He wants to see all open TCP/IP and UDP ports of his computer. Nathan uses the netstat command for this purpose but he is still unable to map open ports to the running process with PID, process name, and path. Which of the following commands will Nathan use to accomplish the task?
Which of the following encryption methods are used by the BlackBerry to provide security to the data stored in it?
Each correct answer represents a complete solution. Choose two.
You work as a professional Computer Hacking Forensic Investigator. A project has been assigned to you to investigate Plagiarism occurred in the source code files of C#. Which of the following tools will you use to detect the software plagiarism?
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
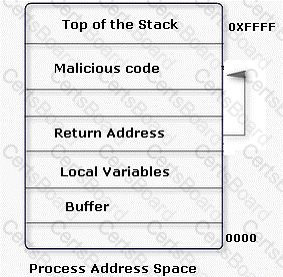
Which of the following tools can be used as a countermeasure to such an attack?
Which of the following statements best describes the string matching method of signature analysis?
Fill in the blank with the appropriate term.
___________ is a technique used to make sure that incoming packets are actually from the networks that they claim to be from.


