John works as a Professional Ethical Hacker for we-are-secure Inc. The company is using a Wireless network. John has been assigned the work to check the security of WLAN of we-aresecure.
For this, he tries to capture the traffic, however, he does not find a good traffic to analyze data. He has already discovered the network using the ettercap tool. Which of the following tools can he use to generate traffic so that he can crack the Wep keys and enter into the network?
Which of the following ports must you filter to check null sessions on your network?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He enters the following command on the
Linux terminal:chmod 741 secure.c
Considering the above scenario, which of the following statements are true?
Each correct answer represents a complete solution. Choose all that apply.
John works as a Penetration Tester in a security service providing firm named you-are-secure Inc.
Recently, John's company has got a project to test the security of a promotional Website
www.missatlanta.com and assigned the pen-testing work to John. When John is performing penetration testing, he inserts the following script in the search box at the company home page:
After pressing the search button, a pop-up box appears on his screen with the text - "Hi, John."
Which of the following attacks can be performed on the Web site tested by john while considering the above scenario?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below:
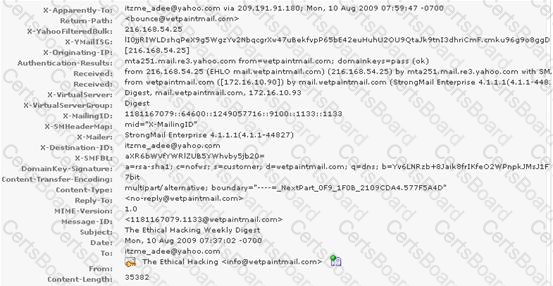
What is the IP address of the sender of this email?
Adam, a malicious hacker, hides a hacking tool from a system administrator of his company by using Alternate Data Streams (ADS) feature. Which of the following statements is true in context with the above scenario?
The employees of EWS Inc. require remote access to the company's Web servers. In order to provide solid wireless security, the company uses EAP-TLS as the authentication protocol. Which of the following statements are true about EAP-TLS?
Each correct answer represents a complete solution. Choose all that apply.
John works as a Professional Ethical Hacker for we-are-secure Inc. The company is using a Wireless network. John has been assigned the work to check the security of WLAN of we-aresecure.
For this, he tries to capture the traffic, however, he does not find a good traffic to analyze data. He has already discovered the network using the ettercap tool. Which of the following tools can he use to generate traffic so that he can crack the Wep keys and enter into the network?
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. John has gained the access to the network of the organization and placed a backdoor in the network. Now, he wants to clear all event logs related to previous hacking attempts. Which of the following tools can John use if we-are-secure.com is using the Windows 2000 server?
Each correct answer represents a complete solution. Choose two.
Which of the following characters will you use to check whether an application is vulnerable to an SQL injection attack?