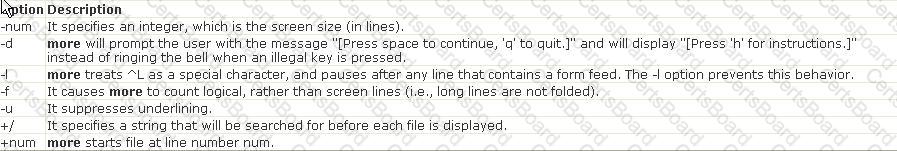
Explanation: The Unix utility sed (stream editor) is a text editing tool that can be used to edit text files without having to open them. This utility parses text files and implements a programming language which can apply textual transformations to such files. It reads input files line by line (sequentially), applying the operation which has been specified via the command line (or a sed script), and then outputs the line. Answer: D is incorrect. The more command is used to view (but not modify) the contents of a text file on the terminal screen at a time. The syntax of the more command is as follows: more [options] file_name Where,
 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG
Answer: A is incorrect. The less command is used to view (but not change) the contents of a text file, one screen at a time. It is similar to the more command. However, it has the extended capability of allowing both forwarB, Dackward navigation through the file. Unlike most Unix text editors/viewers, less does not need to read the entire file before starting; therefore, it has faster load times with large files. The command syntax of the less command is as follows: less [options] file_name Where,
 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG
Answer: C is incorrect. The vi editor is an interactive, cryptic, and screen-based text editor used to create and edit a file. It operates in either Input mode or Command mode. In Input mode, the vi editor accepts a keystroke as text and displays it on the screen, whereas in Command mode, it interprets keystrokes as commands. As the vi editor is case sensitive, it interprets the same character or characters as different commands, depending upon whether the user enters a lowercase or uppercase character. When a user starts a new session with vi, he must put the editor in Input mode by pressing the "I" key. If he is not able to see the entered text on the vi editor's screen, it means that he has not put the editor in Insert mode. The user must change the editor to Input mode before entering any text so that he can see the text he has entered.