Which of the following is a formal state transition model of computer security policy that is used to describe a set of access control rules which use security labels on objects and clearances for subjects?
The disciplined and structured process, that integrates information security and risk management activities into the System Development Life Cycle, is provided by the risk management framework.
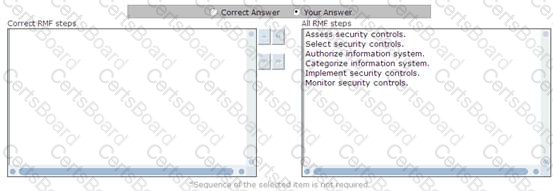
Choose the appropriate RMF steps.
Which of the following are the various types of risk analysis?
Each correct answer represents a complete solution. Choose all that apply.
Single Loss Expectancy (SLE) represents an organization's loss from a single threat. Which of the following formulas best describes the Single Loss Expectancy (SLE)?
You work as an Information Security Manager for uCertify Inc. You are implementing an asset management strategy. Which of the following should you include in your strategy to make it effective?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following policies is a set of rules applied by the owner/manager of a network, Website or large computer system that restrict the ways in which the network site or system may be used?
Which of the following paragraphs of the Turnbull Report stated that a company's system of internal control will include information and communication processes?
Which of the following honeypots provides an attacker access to the real operating system without any restriction and collects a vast amount of information about the attacker?
Mark is the project manager of the NHQ project in StarTech Inc. The project has an asset valued at $195,000 and is subjected to an exposure factor of 35 percent. What will be the Single Loss Expectancy of the project?


