Which of the following are the activities of Incident Management?
Each correct answer represents a complete solution. Choose all that apply.
What are the basic steps involved in Continuity Management?
1. Prioritizing the businesses to be recovered by conducting a Business Impact Analysis (BIA).
2. Performing a Risk Assessment (aka Risk Analysis) for each of the IT Services to identify the assets, threats, vulnerabilities, and countermeasures for each service.
3. Evaluating the options for recovery.
4. Producing the Contingency Plan.
5. Testing, reviewing, and revising the plan on a regular basis.
Each correct answer represents a complete solution. Choose two.
Which of the following represents the software component of IT asset management?
You work as an Information Security Manager for uCertify Inc. You are working on asset management. You need to make a document on the classification of information assets. Which of the following controls of the ISO standard provides guidelines on the classification of information?
Fill in the blank with the appropriate term.
______is the process of managing user authorizations based on the ITU-T Recommendation X.509.
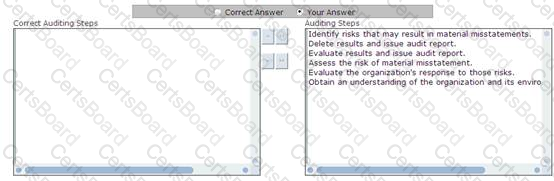
You work as a Network Auditor for Net Perfect Inc. The company has a Windows-based network. You need to audit the network of the company. You need to plan the audit process to minimize the audit risk.
What steps will you take to minimize the possibility of audit risk?
You work as a Network Security Administrator for uCertify Inc. You feel that someone has accessed your computer and used your e-mail account. To check whether there is any virus installed into your computer, you scan your computer but do not find any illegal software. Which of the following types of security attacks generally runs behind the scenes on your computer?


