John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He receives the following e-mail:
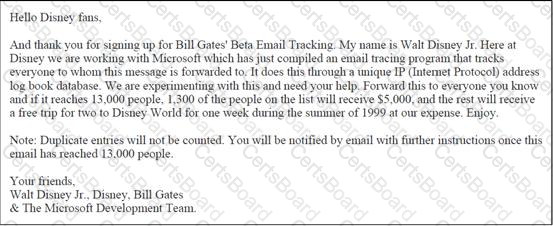
The e-mail that John has received is an example of __________.
You work as an Exchange Administrator for McRobert Inc. You are configuring a new Exchange 2000 Server computer and two storage groups, group A and group B, on your network. You have to configure the physical disks on the Exchange 2000 Server computer to provide better performance and availability. Which configuration will you use to achieve this?
Which of the following statements about Public Key Infrastructure (PKI) are true?
Each correct answer represents a complete solution. Choose two.
A Web developer with your company wants to have wireless access for contractors that come in to work on various projects. The process of getting this approved takes time. So rather than wait, he has put his own wireless router attached to one of the network ports in his department. What security risk does this present?
In what type of attack does an attacker capture packets containing passwords or digital signatures whenever packets pass between two hosts on a network?
Your Company is receiving false and abusive e-mails from the e-mail address of your partner company. When you complain, the partner company tells you that they have never sent any such e-mails. Which of the following types of cyber crimes involves this form of network attack?
Dawn is the project manager of the HQQ Project and she believes the project work is done. She has prepared the final project report, which includes information on the financial performance, schedule performance, and project team performance in the project. All of the following documents are used to measure the completeness of the project scope except for which one?
John works as a Network Administrator for We-are-secure Inc. The We-are-secure server is based on Windows Server 2003. One day, while analyzing the network security, he receives an error message that Kernel32.exe is encountering a problem. Which of the following steps should John take as a countermeasure to this situation?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The company's network is connected to the Internet through a T1 line. The firewall is configured on the network for securing the internal network from the intruders on the Internet. The functional level of the forest is Windows Server 2008. You are designing a public key infrastructure (PKI) for the network. The network will use a root enterprise certificate authority (CA) and a subordinate CA. The root CA will be used to issue certificates to the subordinate CA, and the subordinate CA will be used to issue certificates to the clients.
The management of the company wants to ensure that the security of high-level CAs is not compromised. Which of the following steps will you take to accomplish the task?
You have just set up a wireless network for customers at a coffee shop. Which of the following are good security measures to implement?
Each correct answer represents a complete solution. Choose two.


