You work as a professional Ethical Hacker. You are assigned a project to test the security of www.weare-secure.com. You are working on the Windows Server 2003 operating system. You suspect that your friend has installed the keyghost keylogger onto your computer. Which of the following countermeasures would you employ in such a situation?
Each correct answer represents a complete solution. Choose all that apply.
Your customer wants the fastest wireless possible in his home. Which of the following would you recommend?
Fill in the blank with the appropriate term.
NOTE. Do not use abbreviation.
________ is a configurable client identification that allows a client to communicate with a particular base station.
When no anomaly is present in an Intrusion Detection, but an alarm is generated, the response is known as __________.
You work as a Software Developer for PassGuide Inc. The company uses Visual Studio.NET as its application development platform. You create an application using .NET Framework. You use the application to create an assembly. Now you need to encrypt assembly data. The company has not provided encryption requirements to you. Which of the following symmetric cryptography classes will you use to accomplish this task?
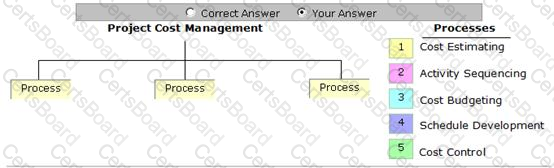
Place the processes that are grouped under the Project Cost Management Knowledge Area in the image below.

The 3-way handshake method is used by the TCP protocol to establish a connection between a client and the server. It involves three steps:
1. In the first step, a SYN message is sent from a client to the server.
2. In the second step, a SYN/ACK message is sent from the server to the client.
3. In the third step, an ACK (usually called SYN-ACK-ACK) message is sent from the client to the server. At this point, both the client and the server have received acknowledgements of the TCP connection. If the Initial Sequence Numbers of the client and server were 241713111 and 241824111 respectively at the time when the client was sending the SYN message in the first step of the TCP 3-way handshake method, what will be the value of the acknowledgement number field of the server's packet when the server was sending the SYN/ACK message to the client in the second step of the TCP 3-way handshake method?
You are the program manager for your project. You are working with the project managers regarding the procurement processes for their projects. You have ruled out one particular contract type because it is considered too risky for the program. Which one of the following contract types is usually considered to be the most dangerous for the buyer?
Which of the following federal laws are related to hacking activities?
Each correct answer represents a complete solution. Choose three.


