Refer to the exhibit, which shows diagnostic output.

A customer reports that ICMP traffic flow from 192.168.1.11 to 93.190.134.171 is not corresponding to the SD-WAN setup.
What is the problem in this scenario?
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:

Based on this configuration, which authentication scenario will FortiGate deny?
Refer to the exhibit that shows VPN debugging output.

The VPN tunnel between headquarters and the branch office is not being established.
What is causing the problem?
Refer to the exhibit.
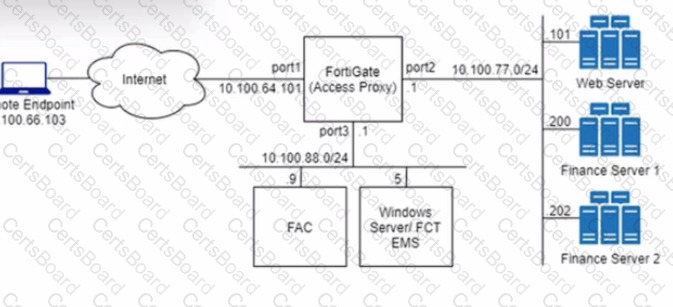
An HTTPS access proxy is configured to demonstrate its function as a reverse proxy on behalf of the web server it is protecting. It verifies user identity, device identity, and trust context, before granting access to the protected source. It is assumed that the FortiGate EMS fabric connector has already been successfully connected.
You need to ensure that ZTNA access through the FortiGate will redirect users to the FortiAuthenticator to perform username/password and multifactor authentication to validate access prior to accessing resources behind the FortiGate.
In this scenario, which two further steps need to be taken on the FortiGate? (Choose two.)
Refer to the exhibit.

The exhibit shows the forensics analysis of an event detected by the FortiEDR core
In this scenario, which statement is correct regarding the threat?
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI. Which two options will prevent this situation in the future? (Choose two)
Refer to the exhibit showing a firewall policy configuration.
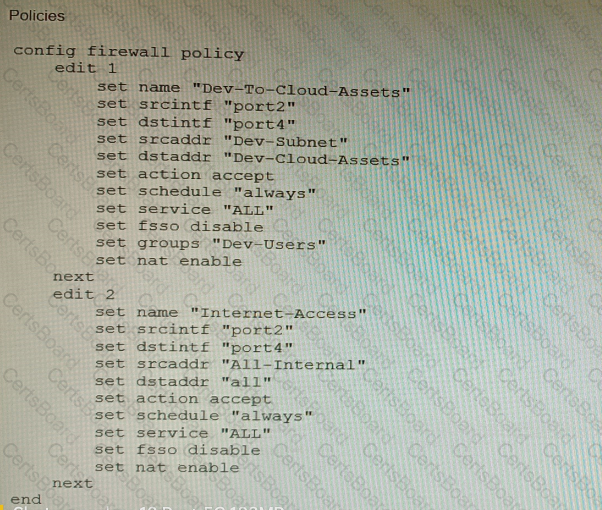
To prevent unauthorized access of their cloud assets, an administrator wants to enforce authentication on firewall policy ID 1.
What change does the administrator need to make?

Refer to the exhibit.

A customer needs to create a multi-tier MCLAG set up with the topology as shown in the exhibit.
A1/A2
B1/B2
C1/C2
Which command snippet should be applied to it, to allow active/active links in this topology?
A Hub FortiGate is connecting multiple branch FortiGate devices separating the traffic centrally in unique VRFs. Routing information is exchanged using BGP between the Hub and the Branch FortiGate devices.
You want to efficiently enable route leaking of specific routes between the VRFs.
Which two steps are required to achieve this requirement? (Choose two.)


