E-mail tracking is a method to monitor and spy the delivered e-mails to the intended recipient.
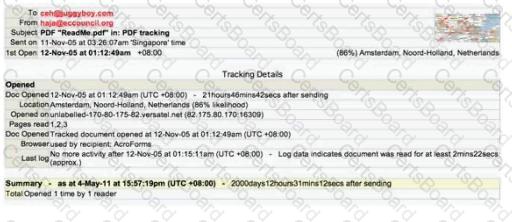
Select a feature, which you will NOT be able to accomplish with this probe?
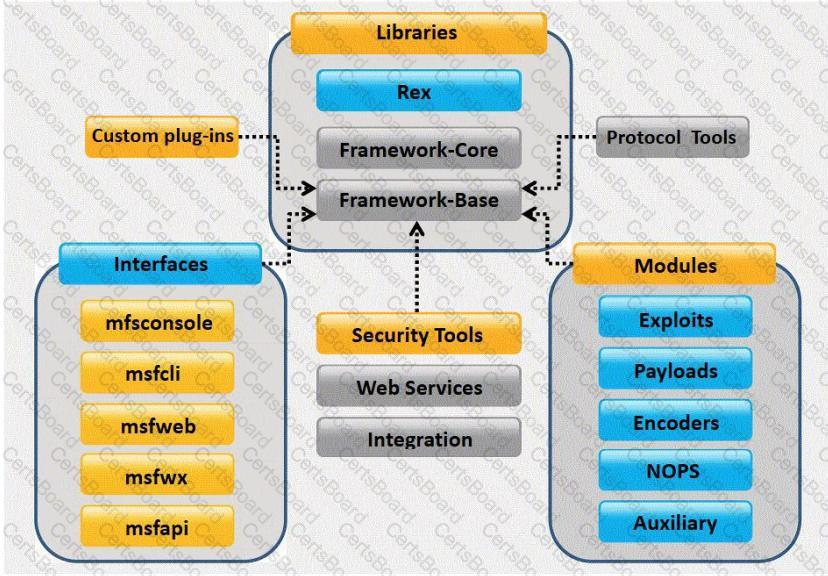
What framework architecture is shown in this exhibit?
NetBIOS over TCP/IP allows files and/or printers to be shared over the network. You are trying to intercept the traffic from a victim machine to a corporate network printer. You are attempting to hijack the printer network connection from your laptop by sniffing the wire. Which port does SMB over TCP/IP use?
You are gathering competitive intelligence on an organization. You notice that they have jobs listed on a few Internet job-hunting sites. There are two jobs for network and system administrators. How can this help you in foot printing the organization?


