What is a security feature available with Windows Vista and Windows 7 that was not present in previous Windows operating systems?
If Linux server software is a requirement in your production environment which of the following should you NOT utilize?
What requirement must an administrator remember when utilizing Security Configuration and Analysis (SCA) to apply security templates to Windows systems?
If a DNS client wants to look up the IP address for good.news.com and does not receive an authoritative reply from its local DNS server, which name server is most likely to provide an authoritative reply?
A system administrator sees the following URL in the webserver logs:
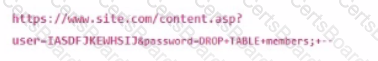
Which action will mitigate against this attack?
Dilbert wants to have a script run on his Windows server every time Wally logs into it. Where should he place this script?
A Windows administrator wants to automate local and remote management tasks in Active Directory. Which tool is most appropriate for this?
In order to capture traffic for analysis, Network Intrusion Detection Systems (NIDS) operate with network cards in what mode?
During which of the following steps is the public/private key-pair generated for Public Key Infrastructure (PKI)?
Which of the following is a benefit of using John the Ripper for auditing passwords?