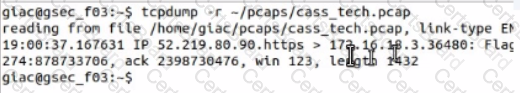
Open the MATE terminal and use the tcpdump program to read - /pcaps /cass tech.pcap.
What is the source port number?
Which of the following are advantages of Network Intrusion Detection Systems (NIDS)?
During a scheduled evacuation training session the following events took place in this order:
1. Evacuation process began by triggering the building fire alarm.
2a. The meeting point leader arrived first at the designated meeting point and immediately began making note of who was and was not accounted for.
2b. Stairwell and door monitors made it to their designated position to leave behind a box of flashlights and prop the stairway doors open with a garbage can so employees can find exits and dispose of food and beverages.
2c. Special needs assistants performed their assigned responsibility to help employees out that require special assistance.
3. The safety warden communicated with the meeting point leader via walkie talkie to collect a list of missing personnel and communicated this information back to the searchers.
4. Searchers began checking each room and placing stick-it notes on the bottom of searched doors to designate which areas were cleared.
5. All special need assistants and their designated wards exited the building.
6. Searchers complete their assigned search pattern and exit with the Stairwell/door monitors.
Given this sequence of events, which role is in violation of its expected evacuation tasks?
Which of the following statements regarding the Secure Sockets Layer (SSL) security model are true?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for NetTech Inc. To ensure the security of files, you encrypt data files using Encrypting File System (EFS).
You want to make a backup copy of the files and maintain security settings. You can backup the files either to a network share or a floppy disk. What will you do to accomplish this?
Which of the following groups represents the most likely source of an asset loss through the inappropriate use of computers?
Which AWS service integrates with the Amazon API Gateway to provision and renew TLS encryption needs for data in transit?
Training an organization on possible phishing attacks would be included under which NIST Framework Core guidelines?