Which of the following consists of the security identifier number (SID) of your user account, the SID of all of your groups and a list of all your user rights?
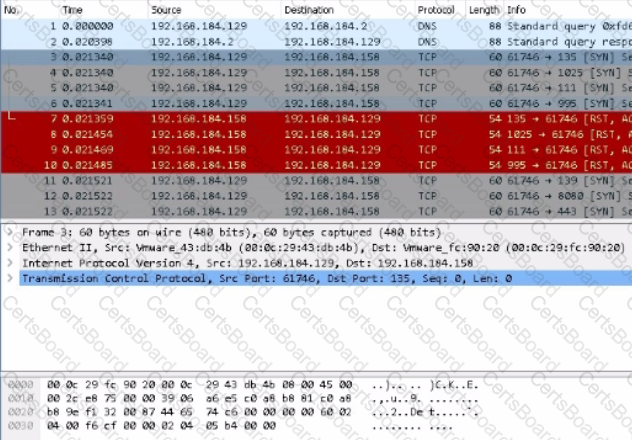
Use Wireshark to analyze Desktop;PCAP FILES/charile.pcap
What is the destination IP address in packet #3?
A database is accessed through an application that users must authenticate with, on a host that only accepts connections from a subnet where the business unit that uses the data is located. What defense strategy is this?
If a Linux administrator wanted to quickly filter out extraneous data and find a running process named RootKit, which command could he use?
An email system administrator deploys a configuration blocking all inbound and outbound executable files due to security concerns.
What Defense in Depth approach is being used?
In preparation to do a vulnerability scan against your company's systems. You've taken the steps below:
You've notified users that there will be a system test.
You've priontized and selected your targets and subnets.
You've configured the system to do a deep scan.
You have a member of your team on call to answer questions.
Which of the following is a necessary step to take prior to starting the scan?