The user of the Accounting workstation reported thattheir calculator repeatedly opens without their input.
Perform a query of startup items for the agent.nameaccounting-pc in the SIEM for the last 24 hours. Identifythe file name that triggered RuleName SuspiciousPowerShell. Enter your response below. Your responsemust include the file extension.
Question 1 and 2
You have been provided with authentication logs toinvestigate a potential incident. The file is titledwebserver-auth-logs.txt and located in theInvestigations folder on the Desktop.
Which IP address is performing a brute force attack?
What is the total number of successful authenticationsby the IP address performing the brute force attack?
Which ruleset can be applied in the
/home/administrator/hids/ruleset/rules directory?
Double-click each image to view it larger.
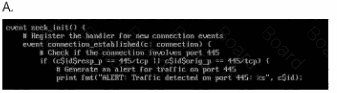
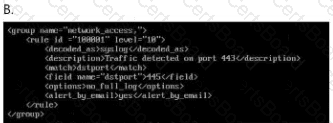
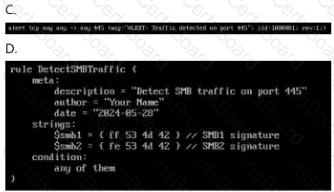
Your enterprise has received an alert bulletin fromnational authorities that the network has beencompromised at approximately 11:00 PM (Absolute) onAugust 19, 2024. The alert is located in the alerts folderwith filename, alert_33.pdf.
What is the name of the suspected malicious filecaptured by keyword process.executable at 11:04 PM?
Cyber Analyst Password:
For questions that require use of the SIEM, pleasereference the information below:
https://10.10.55.2
Security-Analyst!
CYB3R-4n4ly$t!
Email Address:
ccoatest@isaca.org
Password:Security-Analyst!
The enterprise has been receiving a large amount offalse positive alerts for the eternalblue vulnerability. TheSIEM rulesets are located in
/home/administrator/hids/ruleset/rules.
What is the name of the file containing the ruleset foreternalblue connections? Your response must includethe file extension.
Analyze the file titled pcap_artifact5.txt on the AnalystDesktop.
Decode the contents of the file and save the output in atext file with a filename of pcap_artifact5_decoded.txton the Analyst Desktop.
Analyze the file titled pcap_artifact5.txt on the AnalystDesktop.
Decode the C2 host of the attack. Enter your responsebelow.
Your enterprise SIEM system is configured to collect andanalyze log data from various sources. Beginning at12:00 AM on December 4, 2024, until 1:00 AM(Absolute), several instances of PowerShell arediscovered executing malicious commands andaccessing systems outside of their normal workinghours.
What is the physical address of the web server that wastargeted with malicious PowerShell commands?
The CISO has received a bulletin from law enforcementauthorities warning that the enterprise may be at risk ofattack from a specific threat actor. Review the bulletin
named CCOA Threat Bulletin.pdf on the Desktop.
Which host IP was targeted during the following timeframe: 11:39 PM to 11:43 PM (Absolute) on August 16,2024?
An employee has been terminated for policy violations.Security logs from win-webserver01 have been collectedand located in the Investigations folder on theDesktop as win-webserver01_logs.zip.
Create a new case in Security Onion from the win-webserver01_logs.zip file. The case title is WindowsWebserver Logs - CCOA New Case and TLP must beset to Green. No additional fields are required.


