Given the following output from a Linux machine:
file2cable –i eth0 -f file.pcap
Which of the following BEST describes what a security analyst is trying to accomplish?
During a review of security controls, an analyst was able to connect to an external, unsecured FTP server from a workstation. The analyst was troubleshooting and reviewed the ACLs of the segment firewall the workstation is connected to:
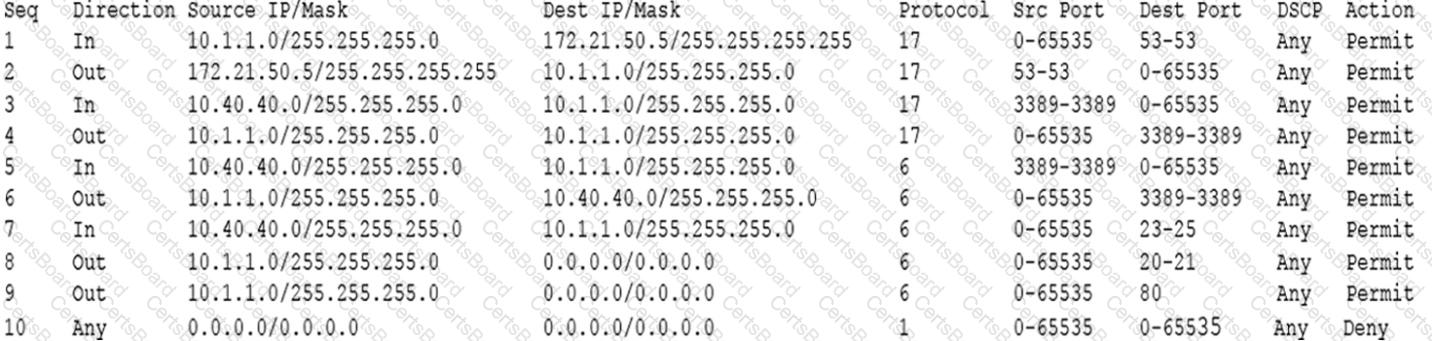
Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?
A technician receives the following security alert from the firewall’s automated system:
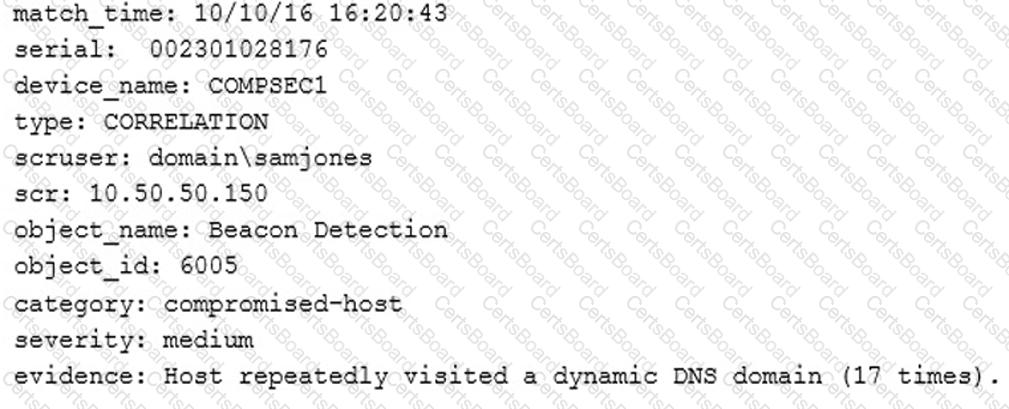
After reviewing the alert, which of the following is the BEST analysis?
A security analyst is concerned that employees may attempt to exfiltrate data prior to tendering their resignations. Unfortunately, the company cannot afford to purchase a data loss prevention (DLP) system. Which of the following recommendations should the security analyst make to provide defense-in-depth against data loss? (Select THREE).


