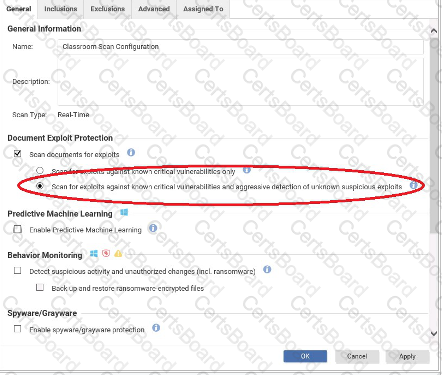
Based on the configuration setting highlighted in the exhibit, what behavior can be expected during a malware scan?
A Recommendation Scan is run to determine which Intrusion Prevention rules are appropriate for a Server. The scan is configured to apply the suggested rules automatically and ongoing scans are enabled. Some time later, an operating system patch is applied. How can you de-termine which Intrusion Prevention rules are no longer needed on this Server?
Which of the following statements is true regarding Firewall Rules?
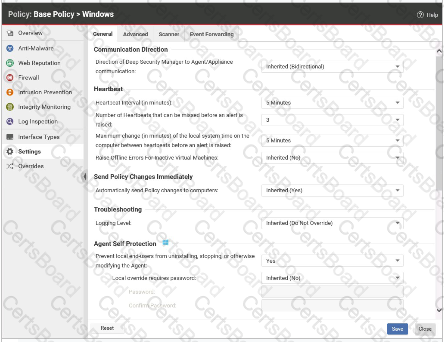
Which of the following statements is correct regarding the policy settings displayed in the exihibit?