A company disables cd drives for users; what defense strategy is this a part of?
Which of the following proxy servers provides administrative controls over the content?
What is the key difference between Electronic Codebook mode and other block cipher modes like Cipher Block Chaining, Cipher-Feedback and Output-Feedback?
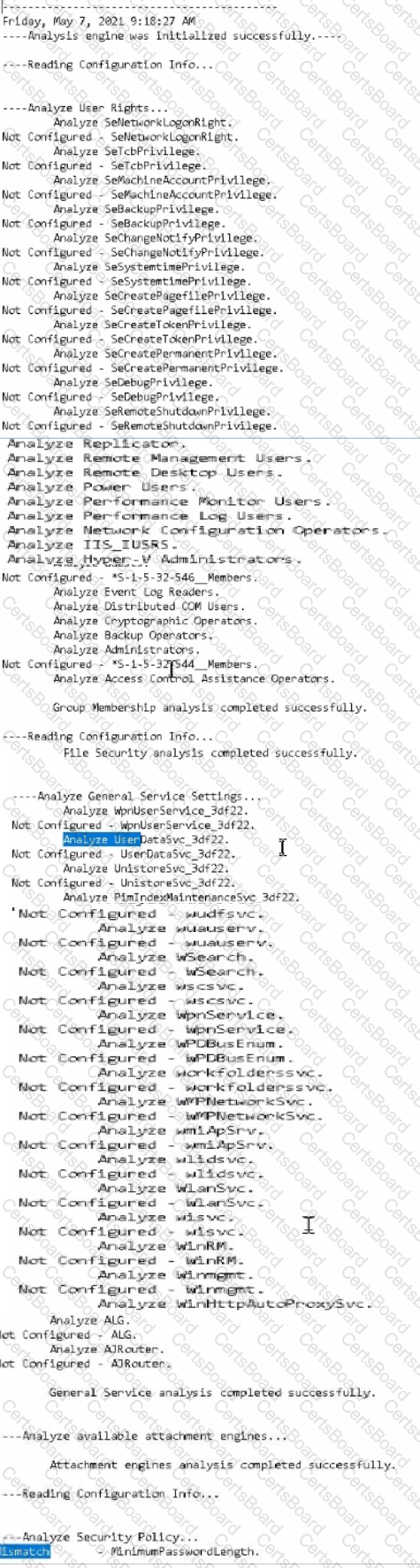
Using PowerShell ISE running as an Administrator, navigate to the
C:\hlindows\security\tevplatesdirectory. Use secedit.exe in analyze mode to compare the temp.sdb and uorkstdtionSecureTmplate.inf files, and output the findings to a file called log.txt. Which configuration setting under Analyze User Rights reports a mismatch?
Hints:
Use files located in the C \windows\security\templates\ directory
The log. txt file will be created in the directory the secedit.exe command is run from

Which of the following is a signature-based intrusion detection system (IDS) ?
In an Active Directory domain, which is the preferred method of keeping host computers patched?
Which of the four basic transformations in the AES algorithm involves the leftward circular movement of state data?