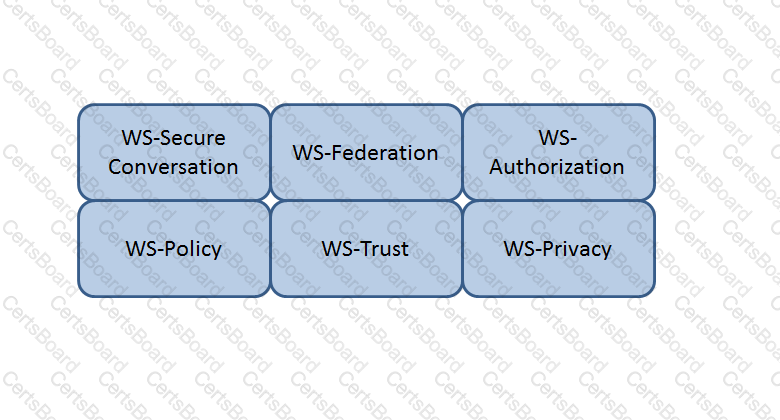
Which Web Services Security (WS-Security) specification handles the management of security tokens and the underlying policies for granting access? Click on the correct specification in the image below.
Which of the following controls is the FIRST step in protecting privacy in an information system?
A user sends an e-mail request asking for read-only access to files that are not considered sensitive. A Discretionary Access Control (DAC) methodology is in place. Which is the MOST suitable approach that the administrator should take?
Which one of the following activities would present a significant security risk to organizations when employing a Virtual Private Network (VPN) solution?


