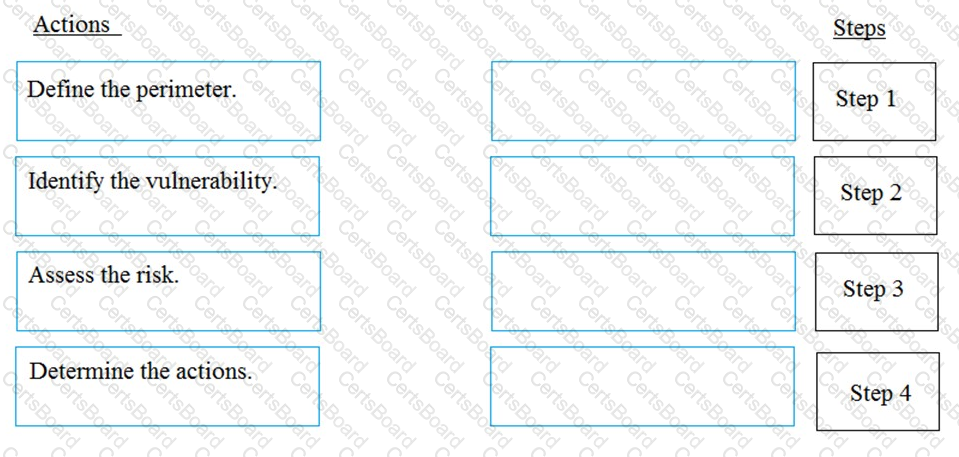
What is the correct order of steps in an information security assessment?
Place the information security assessment steps on the left next to the numbered boxes on the right in the
correct order.
Which of the following is a benefit in implementing an enterprise Identity and Access Management (IAM) solution?
A company receives an email threat informing of an Imminent Distributed Denial of Service (DDoS) attack
targeting its web application, unless ransom is paid. Which of the following techniques BEST addresses that threat?
Which of the following alarm systems is recommended to detect intrusions through windows in a high-noise, occupied environment?


